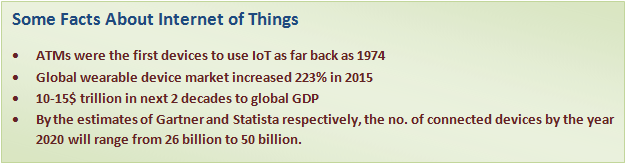
Internet of Things Explained-Yes, It's Simple
You might have encountered people who claim to have read Tolstoy or watched The Godfather, but in reality, only a few of them actually have. Likewise, Internet of Things (IoT) too, has become the technology buzzword that many around you will use in their sentences to make an impact, but fumble for words when you’ll ask for a simple explanation. Using a popular term without knowing its meaning is bandwagon effect and more prevalant than you think. Although it’s really strange why there is confusion regarding IOT's meaning, because when you look at it, the name itself kind of gives it away.
The Definition of IoT
Understanding IoT (Internet of Things) is simple - You have human beings sitting on the internet and sharing their pictures that no one really wants to see (except 3 or 4 close friends). This is how you understand the normal Internet or Internet of Beings.
Now imagine devices connected via internet and sharing info about their lives, which consists of how much battery they have left, if they are facing any technical problem, how much energy they are consuming, etc. They can also share information about their owner if they have been programmed to do so. Such a network of interconnected devices communicating with each other, sharing and reacting to the information by interpreting it, is called Internet of Things.
What Constitutes a “Thing” in Internet of Things?
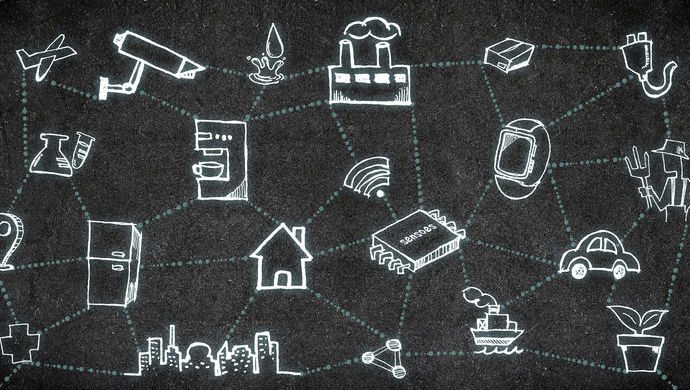
Conventionally, any object that is a smart object has the potential to be a part of the IoT Universe. The multitude of smart objects like your mobile, fitness gadget, self driving car, etc. are already functioning as “things” in the interconnected IoT universe.
These are the prerequisites of converting any object to a smart object, and empowering it to become a member of the IoT Universe-
1. Unique identity (IP Address)
A completely unique identifier for an object in a digital universe is necessary. It determines how that object would be recognized in an interconnected network. An IP address serves this function, like your home’s postal address, in a network of interconnected devices.
Note-With the gradual incorporation of IPv6 replacing IPv4,the number of possible IP addresses has increased from 2^32 to 2^128. This gargantuan amount of IPv6 addresses that are and will be available to the coming generation of devices will boost the growth of Internet of Things and mark the beginning of a new digital future.
2. Ability to communicate
The object must have an ability to connect/communicate with a network. It means a feature that can help the object to connect with a local or wide area network (internet), like a wireless connection. In fact, you encounter numerous wireless enabled devices in your life every day.
3. The Object must have senses
The ability to sense the surroundings or a stimulus and react to it is possible only if an object has some kind of audio/visual/physical sensors that can sense and transmit that information.
4. Ability to control the smart device remotely
Finally, we need to embed the smart object with an IC that enables us, or any other controlling mechanism, to control it remotely without being in the physical vicinity of the object.
What is the Scope of IoT?

The scope of IoT is irrefutably in its favor. IoT can easily make our lives simpler, optimized and efficient. In fact, it can minimize the wastage, conserve resources and truly enable a society that works on the principle of sustainable development.
Here are a few things that can happen or are happening-
- Connecting with things in a manner that our devices can gather all the information of the other device (object) or the individual operating that device by just being in the vicinity of that object. Remember the famous cartoon DragonBall Z, it is exactly like Vegeta’s Scouter, which he used to examine the power level of his opponents.
- Monitoring your life and different aspects of it, like smartphone apps that monitor pulse and heart rate, breathing, etc. Such monitoring techniques coupled with powerful algorithms involving patient history could predict health issues/ vulnerabilities beforehand. Healthcare sector could see a possible upsurge in this.
- Reality search engines, that is, when every object would be tagged and a part of interconnected network of the IoT universe. Forget about losing your keys ever again. (Black Mirror Geek warning - Even human beings could become a commodity).
- Manage multiple things and individuals at a time. Get minute to minute updates of your health, status of your devices or the location of individuals thereby enabling you to keep your health, life and relations up to date. In fact, the idea of dynamic traffic management in a smart city with the help of a network of interconnected cars is not too distant in the future.
- Control other devices using a smart object to efficiently optimize their use and reduce wastage of resources. You might have heard about smart meters that control every device in your home and decide when to switch on and off a device based on the perfect balance of load and energy efficiency.
- Play Virtual Reality (VR) games like Pokemon Go. Virtual Reality has turned everyday world into a playing arena, and this is just the beginning. The imagination of R&D department of every major gaming company is running wild with ideas to create more immersive gameplay for the users employing VR technology.
Concerns with IoT – Privacy and Security

It is highly unlikely that while reading the amazing features of IoT you didn’t squint your eyes once with skepticism over the privacy and security concerns. Yes, Internet of Things has a remarkable ability to control and manage the world by analyzing humongous amounts of data, but the very reason that makes it effective is also the reason that raises eyebrows in apprehension. It is the mammoth data stream that is continuously flowing in an IoT universe, which brings up a threat of Data Security and User Privacy.
In fact, the serious Black Mirror fans might have imagined a technological dystopia already. However, what we need is an honest look at the concerns to deal with them in a methodical and effective manner.
Data Security
- Community Outlook
We can very well agree that in the past few years, people have become more cognizant of the possible data breach in their web connected devices. With a slew of cyber attack stories circling in our midst, it is logical to become cautious of any technology that could make user data vulnerable.
- Increased Susceptibility to Hacking
When uncountable devices, connected via a network are working simultaneously, then it becomes less tedious for hackers to find an entry into that network and reach the device, which contains your personal or financial info.
- Are Organizations Prepared?
Although a lot of organizations are planning to deploy full-fledged IoT technologies to get ahead of the curve, they lack confidence in security measures of those IoT devices. Yes, they are definitely working on the solution to the problem and have devised methodologies too, but they lack conviction on the degree of vulnerability of their company to a DDoS attack.
- Multi Step Security
A lot of measures and creative remedies are required to enable data protection in IoT. Security measures need to be in place at the entry, exit and network channel. While the same measures of security must be applied to the applications that would interact and interpret that data.
User Privacy
- Maintaining Privacy in a Colossal Data Stream
Privacy is a big concern in IoT, where you have an interlinked web of complex data streams. The amount of distinct data points generated by a household every day is around 150 million, as quoted by an FTC report on the privacy and security implication of IoT in an interconnected world.
- Victim of an Aggressive Market
You must have agreed to so many Terms of Service agreements without giving it a second look. Unwittingly you invite individually focused advertising by giving the right to use the data collected by monitoring your activity to a company. Potential of exploitation by companies increases with increased monitoring. It might happen that a health insurance company increases your premium based on your daily routine.
- Peeping Toms
Apart from a covert attack on the dignity of an individual, multiple entry points in IoT makes it less difficult for hackers to dive into the personal and financial history of that individual, making them vulnerable to coercion and extortion.
- Trust of the Consumer
The most important way to capitalize on this technology, which is of monumental scope, is by building customer confidence in that technology, which is not as good right now. That is only possible by methodically dealing with each and every concern posed by IoT. As we speak, there are already a number of data scientists and technocrats working on creating better measures of security and privacy in IoT.
Now, anyone in their right mind would be apprehensive of such concerns to privacy and security. So what does the road ahead looks like for IoT?
The Road Ahead

Whatever Your Personal Opinion regarding Internet of Things may be, there is one gospel truth that you cannot deny -
It is happening and it is here to stay.
IoT will change our lives for good, or worse if we keep living in denial, but the writing on the wall is clear, and it is positive. We have started working as a community to make IoT more secure, transparent and efficient. In fact, its efficiency is already generating profit for approximately 5000 companies across the globe, which have started using IoT devices actively in their business operations. It’s really a wonder, still why so many people and companies are shying away from IoT and its possible use in their lives and businesses.
The World Economic Forum (WEF) at Davos clearly enunciated the onus of change lies with the technology industry and big businesses. It outlined the need for forward and backward transparency, which means, user must know whenever his/ her personal data is being used as well as how the company is using that information. Of course, these were just suggestions and not binding orders.
Global IT community has shown commitment and is busy in researching and developing IoT into a more secure and transparent phenomenon. This collective effort on such a large scale shows our resolve to making an era of an omnipresent IoT universe possible in the next decade. Visionary CEOs have already invested their fair share in developing nuanced IoT devices and services, which shows how big of a phenomenon it could be. However, its complete success will be truly enabled by an aware user, who can compel the businesses to provide services with utmost regard for user’s privacy and security.
Remember, with great user awareness comes great business integrity.